Welcome, dear reader, to an exploration of the ever-evolving landscape of cybersecurity measures in the realm of operational technology. In today’s world, where technology plays a critical role in the functioning of various industries, protecting operational systems from cyber threats has become more vital than ever. From manufacturing plants to energy facilities, the security of operational technology is paramount to ensuring smooth operations and safeguarding sensitive data. Let’s dive into the strategies and advancements aimed at enhancing cybersecurity in the realm of operational technology.
Understanding the Threat Landscape in Operational Technology
Operational Technology (OT) refers to the hardware and software that controls industrial operations such as manufacturing, transportation, and infrastructure. These systems are essential for the functioning of critical infrastructure and are increasingly being connected to the internet for remote monitoring and control. While this connectivity offers many benefits, it also introduces new risks and vulnerabilities that can be exploited by cyber attackers.
One of the key threats facing OT systems is the increasing sophistication of cyber attacks. In the past, attacks on OT systems were relatively rare and often opportunistic. However, as the number of connected devices in industrial environments has grown, so too has the interest of cyber criminals in targeting these systems. Attackers are now using more advanced tactics such as ransomware, phishing, and supply chain attacks to compromise OT systems and disrupt operations.
Another significant threat to OT cybersecurity is the convergence of IT and OT networks. Historically, these networks have been kept separate to prevent cyber attacks on one from affecting the other. However, many organizations are now integrating their IT and OT systems to improve efficiency and reduce costs. While this integration can bring benefits, it also creates new avenues for attackers to infiltrate OT systems and cause serious damage.
Attacks on OT systems can have far-reaching consequences, including physical damage, loss of life, and environmental damage. For example, an attack on a power plant could result in a widespread blackout that affects homes, businesses, and critical infrastructure. Similarly, an attack on a transportation network could lead to accidents and disruptions that endanger lives and cause economic losses.
In addition to external threats, organizations also need to be aware of insider threats to their OT systems. Employees with malicious intent or insufficient training can pose a significant risk to the security of OT systems. These insider threats can be particularly difficult to detect and mitigate, as they often have legitimate access to the systems they are targeting.
Overall, the threat landscape in operational technology is constantly evolving, with attackers becoming more sophisticated and organizations facing new challenges in securing their OT systems. To effectively defend against these threats, organizations need to implement robust cybersecurity measures, including regular security assessments, employee training, and the use of advanced security technologies. By staying vigilant and proactive, organizations can protect their OT systems from cyber attacks and ensure the safety and reliability of their operations.
Best Practices for Securing Operational Technology Systems
When it comes to securing operational technology (OT) systems, there are several best practices that organizations can implement to protect their critical infrastructure. One key practice is to conduct regular cybersecurity assessments and audits to identify vulnerabilities and weaknesses within the OT environment. By proactively assessing the security posture of the OT systems, organizations can better understand their risk exposure and take appropriate measures to mitigate potential threats.
Another important best practice is to implement strong access controls and authentication mechanisms to prevent unauthorized access to OT systems. This can involve implementing multi-factor authentication, role-based access controls, and strong password policies to ensure that only authorized personnel are able to access and modify OT systems. Additionally, organizations should regularly review and update access permissions to ensure that former employees or contractors do not retain access to critical OT systems.
Furthermore, organizations should prioritize network segmentation and isolation within their OT environment to limit the impact of a potential cyber attack. By segmenting the OT network into distinct zones and implementing firewalls and intrusion detection systems, organizations can contain and prevent the spread of malware or unauthorized access within the OT environment. This also helps to minimize the potential damage and disruption caused by a cyber attack, as it restricts the attacker’s ability to move laterally within the network.
In addition to network segmentation, organizations should also encrypt sensitive data and communications within the OT environment to protect against eavesdropping and tampering. Encryption technologies such as VPNs and secure communication protocols can help safeguard the confidentiality and integrity of data transmitted between OT devices and systems. By encrypting data at rest and in transit, organizations can prevent unauthorized parties from intercepting or modifying critical information.
Moreover, organizations should establish incident response plans and procedures to effectively respond to and recover from cybersecurity incidents within the OT environment. This includes defining roles and responsibilities, conducting regular drills and simulations, and establishing communication protocols with internal teams and external stakeholders. By being prepared to rapidly detect, contain, and remediate cyber threats, organizations can minimize the impact of a security incident on their OT operations.
Lastly, ongoing training and awareness programs for employees and contractors can help reinforce the importance of cybersecurity within the OT environment. By educating personnel on common security risks, best practices, and reporting procedures, organizations can empower their workforce to identify and respond to potential threats in a timely manner. Training programs can also help raise awareness of social engineering tactics and phishing scams that may target OT personnel, reducing the likelihood of a successful cyber attack.
Bridging the Gap Between IT and OT Security
As organizations increasingly rely on operational technology (OT) to drive their day-to-day operations, the need to bridge the gap between IT and OT security has become more pronounced. While traditional IT security focuses on securing networks, servers, and endpoints, OT security deals with securing industrial control systems, sensors, and other devices used in critical infrastructure and manufacturing processes. The convergence of IT and OT systems has created a complex cybersecurity landscape that requires a more integrated approach to security.
One of the key challenges in bridging the gap between IT and OT security is the differing priorities and objectives of the two disciplines. IT security is primarily focused on protecting data confidentiality, integrity, and availability, while OT security is more concerned with ensuring the safe and reliable operation of industrial processes. This fundamental difference in goals can lead to misalignment in security strategies and priorities, making it difficult to effectively secure both IT and OT environments.
To address this issue, organizations need to adopt a holistic approach to cybersecurity that takes into account the unique requirements of both IT and OT systems. This includes establishing clear communication channels between IT and OT teams, as well as developing a shared understanding of the risks and vulnerabilities that exist in each environment. By fostering collaboration and breaking down silos between IT and OT security teams, organizations can better protect their critical infrastructure from cyber threats.
Implementing Effective Incident Response Strategies for OT Cyberattacks
When it comes to protecting operational technology (OT) systems from cyberattacks, having a solid incident response plan in place is crucial. OT systems are becoming increasingly connected, making them more vulnerable to cyber threats. In order to effectively respond to cyber incidents in OT environments, organizations must implement proactive strategies that address both prevention and response measures.
One key aspect of implementing an effective incident response plan for OT cyberattacks is to have a clear understanding of the various types of cyber threats that could impact OT systems. This includes familiarizing yourself with common attack vectors, such as phishing emails, malware injections, and insider threats. By being aware of these potential threats, organizations can better prepare for and respond to cyber incidents when they occur.
In addition to understanding common cyber threats, organizations should also conduct regular risk assessments to identify potential vulnerabilities in their OT systems. By identifying weak points in the system, organizations can take proactive measures to strengthen their defenses and reduce the risk of a successful cyberattack. This may include implementing security patches, updating software, and conducting regular security training for employees.
Another important aspect of effective incident response for OT cyberattacks is to establish clear communication channels within the organization. In the event of a cyber incident, having a designated team of personnel who are trained to respond to such incidents can help to mitigate the damage and limit the impact on OT systems. This team should be responsible for coordinating the response efforts, communicating with stakeholders, and ensuring that the incident is properly managed.
Furthermore, organizations should also consider investing in advanced cybersecurity tools and technologies that can help to detect and mitigate cyber threats in real-time. This may include intrusion detection systems, endpoint security solutions, and network monitoring tools. By leveraging these technologies, organizations can proactively monitor their OT systems for any suspicious activity and respond quickly to potential cyber threats.
In conclusion, implementing effective incident response strategies for OT cyberattacks is essential for protecting critical infrastructure and maintaining operational continuity. By understanding common cyber threats, conducting regular risk assessments, establishing clear communication channels, and investing in advanced cybersecurity technologies, organizations can better prepare for and respond to cyber incidents in their OT environments. Ultimately, a proactive approach to cybersecurity is the key to safeguarding OT systems from malicious cyber threats.
Building a Robust OT Cybersecurity Program
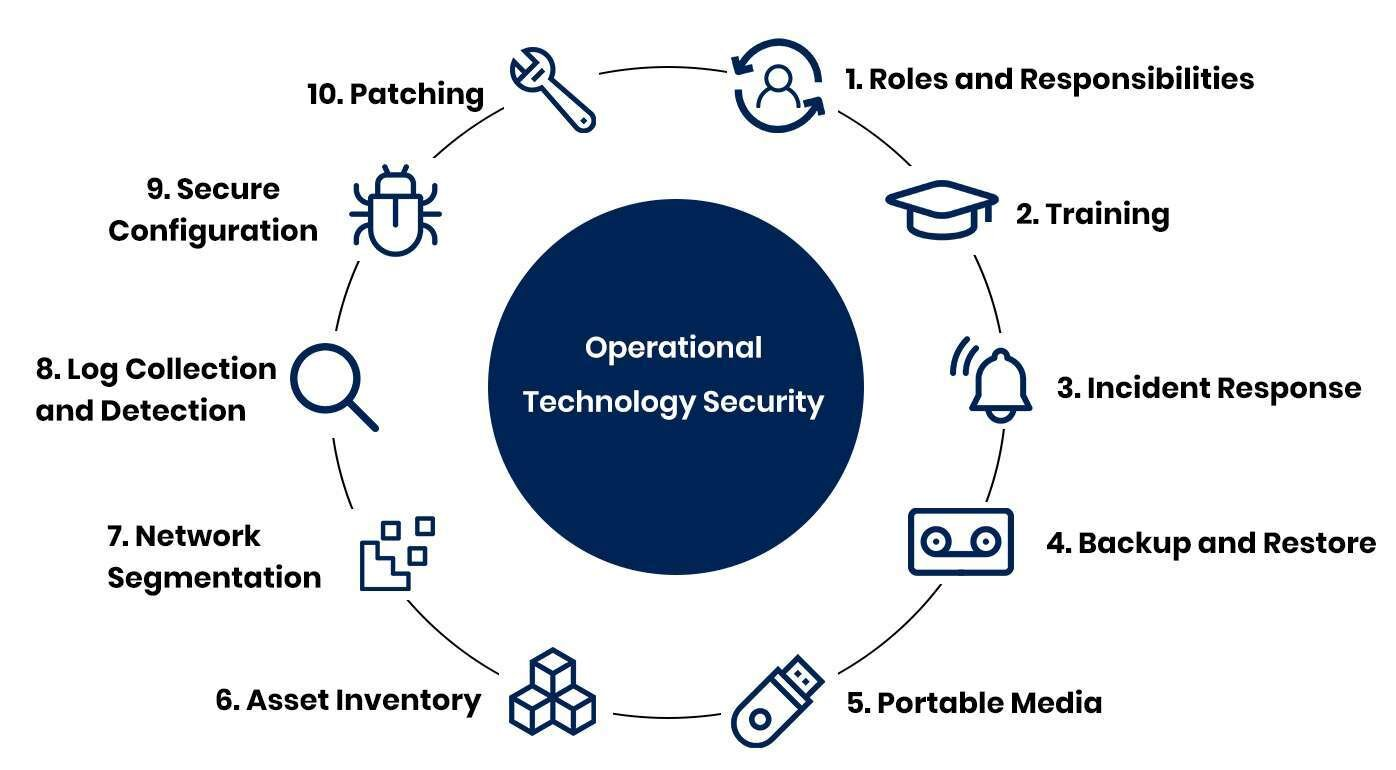
When it comes to operational technology (OT) cybersecurity, having a robust program in place is essential to protect critical infrastructure from cyber threats. A robust cybersecurity program should encompass various layers of defense to ensure the security and integrity of the OT environment. Here are five key components to consider when building a strong OT cybersecurity program:
1. Asset Inventory: The first step in any cybersecurity program is to have a comprehensive inventory of all OT assets within the organization. This includes identifying all devices, systems, and software that are connected to the OT network. Having a detailed asset inventory allows organizations to track and monitor the security posture of their OT environment.
2. Risk Assessment: Conducting regular risk assessments is crucial to understand the potential vulnerabilities and threats facing the OT environment. By identifying and prioritizing risks, organizations can better allocate resources and implement security measures to mitigate potential cyber threats.
3. Access Control: Limiting access to critical OT systems and devices is essential to prevent unauthorized users from compromising the security of the infrastructure. Implementing strong access controls, such as multi-factor authentication and role-based access permissions, can help prevent unauthorized access and limit the impact of cyber attacks.
4. Network Segmentation: Segregating OT networks from IT networks is a best practice to minimize the risk of cyber attacks spreading across the organization. By implementing network segmentation, organizations can isolate OT systems and limit the potential impact of a security breach on critical infrastructure.
5. Incident Response Plan: In the event of a cyber attack or security breach, having a well-defined incident response plan is critical to minimize downtime and mitigate any potential damage. An effective incident response plan should outline the steps to be taken in the event of a security incident, including notifying stakeholders, containing the threat, and restoring operations.
Additionally, organizations should regularly test and update their incident response plan to ensure its effectiveness in addressing current threats and vulnerabilities.
Overall, building a robust OT cybersecurity program requires a combination of proactive measures, such as asset inventory and risk assessments, as well as reactive strategies, such as access control and incident response planning. By implementing these key components, organizations can strengthen their defenses against cyber threats and safeguard their critical infrastructure from potential security breaches.